Overview
This article introduces Security Risk Management process and the main concepts involved in risk management and how risk management is applied to security in an organization.
The terms risk and risk management have been commonly used to apply to other components of risk management, including business continuity, emergency preparedness, and audit. However, despite their increased use, or perhaps because of it, the terms and the processes they encompass are not clearly or commonly understood. That is why it is necessary to explain what Security Risk Management means, why it is crucial to an organization, and how it uses a simple but structured decision-making model to help the organization better achieve its goals.
What is Security Risk Management?
Risk management: The systematic determination and implementation of timely and effective approaches for managing the effects of threats to the organization.
Security Risk Management is a system of identifying future harmful events that may affect the achievement of objectives: assessing them for likelihood and Impact and determining an appropriate response. Any organizational objective, from global strategic goals to local projects, may fail because of various obstacles. In the security context, obstacles are called threats. Therefore, all managers should identify threats and evaluate how these threats may affect their objectives. In many of the places where we work, not just in hostile or volatile environments, the effect of threats, if not managed, can be fatal to staff and activities. On the other hand, Risk is the combination of the likelihood of a threat being carried out and the subsequent Impact on the organization. The process whereby a manager identifies, evaluates, and systematically deals with obstacles to success is risk management. Security measures can either be used to prevent a vulnerability from being exploited or mitigate the Impact of exploitation, or both. One way to think of risk management is that it is the systematic determination and implementation of timely and effective approaches for managing the effects of threats to the organization. Thus, Security Risk Management is merely the management of security-related risks.
Why is it important?
Security Risk Management is an essential management tool. It increases the chances of achieving goals by decreasing the effect of threats. Security Risk Management offers a structured approach to help make good decisions and allows for clear accountability. It allows managers to maximize opportunities and allocate security-related resources in ways that enable delivery within acceptable levels of risk. It is vital to achieving the planned objectives and results for the organizations, especially in complex and dangerous environments.
Definition of Risk
Although the steps of Security Risk Management are clear and simple, it is important to understand what risk is. We advocate and use the concepts of Likelihood and Impact to define Risk; the assessment of Risk, therefore, is an assessment of how vulnerable the organization is to an adverse event (a Threat), expressed in terms of Likelihood (the prospect of the event occurring) and Impact (the effect of the event if it does occur). To illustrate, “risk” is intuitively composed of two components (Likelihood and Impact); take the example of a tightrope walker – most people have little hesitation walking along the top of a table or bench. However, if you raise the table or bench 100 feet (30 meters)s in the air, most people would feel uncomfortable doing the same thing. This is because they intuitively know that the risk has changed. Even though the likelihood of falling off the table is the same in both situations, the Impact (if they were to fall) in the second situation is significantly higher. If the bench is shrunk to the with of a rope, as it is for a tightrope walker, then the likelihood of falling also increases. Thus, the risk of falling is a combination of both the likelihood of falling and the Impact of the fall. Understanding that risk is a combination of likelihood and Impact, it is clear that managing risk is a question of managing likelihood and Impact. A tightrope walker may use a large pole to increase his balance and lower the likelihood of falling. He may also install a net below the tightrope so that the Impact will be less serious if he does fall. In this way, he has managed his risk by managing both likelihood and Impact. When discussing the management of risks, we have adopted the terms Prevention and Mitigation; taking measures to reduce Likelihood is called Prevention, while reducing Impact is called Mitigation. In the Security Risk Management process, Likelihood and Impact have unique definitions, distinct ways of being measured, and a common way of being combined to determine risk. This is explained in greater detail in Step – 5 of this manual. At this point, it is important to understand that Likelihood and Impact are usually assessed on a 1-5 scale and combined in a Risk Matrix. Various similar versions are used; this particular one is used by Grey International and by the United Nations, among others:
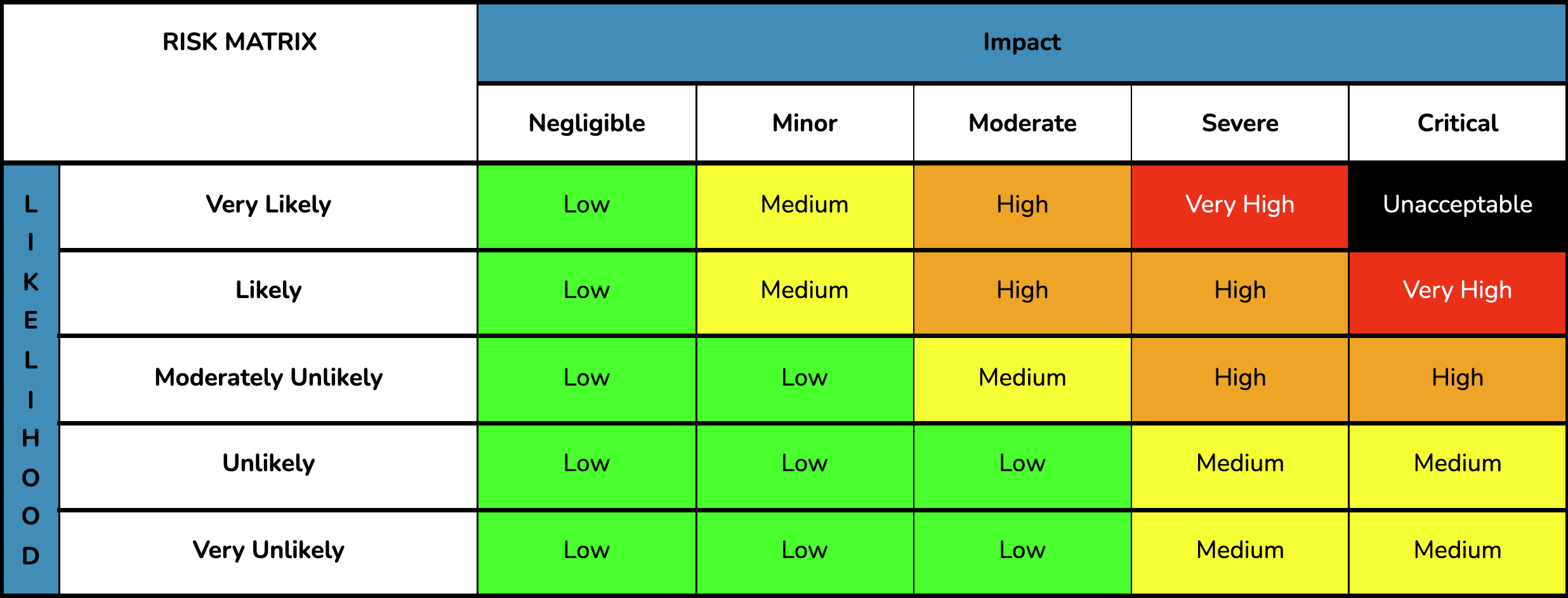
Threat, Risk, and Vulnerability
To conceptualize Threat, Risk, and Vulnerability, it is helpful to use another example, this time involving our ancestors. Generations ago, our human ancestors lived with the genuine danger of attack by predators. They saw members of their communities killed by predators and knew the threat was there. Changes in nomadic life and the environment meant that humans interacted with predators to various degrees and often competed with them for resources. Coexisting in the same environment with predators increased the likelihood that humans would be attacked by these predators, including the possible worst Impact of being killed. In addition, human physical prowess was a significant weakness or vulnerability compared to some predators. What did our ancestors do to manage the risk posed by predators? They probably avoided areas where predators were common, and they developed protection strategies against predators when they needed to gather food or water. Protection strategies could include living in groups, sleeping in trees when traveling, building shelters to keep predators out, and even developing weapons to repel or kill predators when required. Some prevention measures lowered the likelihood of being attacked, such as building shelters, while mitigation measures lowered the Impact if they were attacked, such as communicating between groups to call for help and developing responses to help the injured. They found a balance between what they needed to do and the threat posed by predators through all this. We control our risk by controlling our vulnerability to risks. In this way, risk management aims to lower our Vulnerability, thereby lowering the Likelihood and/or Impact. When we lower the Likelihood through prevention, this is also called changing the “Prevention Vulnerability.” When we lower Impact through mitigation, this is called changing “Mitigation Vulnerability.” Our ancestors’ decision about whether they should go into an area where predators hunt was not based only on the fact that the predators were in the environment. The decision should also reflect a realistic evaluation of a present vulnerability to the threats in that environment (what effective protection measures they had) and the ability to decrease vulnerability through increasing protection. This is one of the most important issues for SRM: Management decisions should not be based on the threat! Only when we are clear on the vulnerability to a threat should we decide what to do next. The decision to go ahead with a given activity would also consider how important the activity is. Our ancestors may have traveled through predator-infested areas to gather food for their children or to come to the aid of others in their communities. They would probably not have taken the same risk to gather items for a cultural ceremony. This is an issue of Acceptable Risk and the balance of risk and benefit (we often refer to “benefit” as Project Criticality). This will be further addressed in ‘Acceptable Risk’ later.
Risk management strategies
Risk management is the process whereby an organization attempts to lower Risk by influencing Likelihood and/or Impact. Because we usually have limited or no influence over the threat, it is best to focus on lowering Risk. Influencing Likelihood and Impact is usually done through what is known as risk controls. There are, however, other ways to manage risk besides just controlling it. There are four main strategies for managing risk (ACAT):
- Accept the risk (no further action)
- Control the risk (using prevention and/or mitigation measures)
- Avoid the risk (temporarily distance the target from the threat)
- Transfer the risk, aka. risk-sharing (insurance, sub-contract, etc.)
These four strategies will be explained in more detail in the ‘Acceptable Risk’ lesson later.
Deliberate vs. Non-Deliberate Events
In assessing and managing risks, it is important to realize the difference between events purposely caused by a motivated human antagonist and acts of nature or accidents. In the SRM process, the former is called “Deliberate Events,” and the latter is called “Non-deliberate Events.” The “cause” of deliberate events is a “threat.” The “cause” of non-deliberate events is a “hazard.” Thus, the concept of “security” covers threats (Deliberate Events), and the concept of “safety” covers hazards (Non-deliberate Events). See Table 1 below.
| Subject | Type of “danger” | Types of events |
| Security | Threat | Deliberate |
| Safety | Hazard | Non-deliberate |
Some hazards are included in the SRM process!
Although most human-caused, deliberate events are covered under the concept of “security,” not all hazards are covered under the “safety” umbrella. We often include three safety areas: road safety, fire safety, and aviation safety in the SRM process. Keep in mind that many other areas of safety are not covered by the SRM process, including medical, occupational health and safety, and structural engineering.
The steps of security risk management
The Security Risk Management process is a structured, problem-solving mechanism: Step 1: Setting the geographical scope and timeframe Where will we be working, and what is the timeframe for the analysis? Step 2: Situational Analysis What is the overall security situation in that area? Step 3: Project Assessment What are the main goals and posture in that area? Step 4: Threat Assessment (General & Specific) What are the obstacles to achieving goals? Step 5: Security Risk Assessment How vulnerable is the Organization to these threats? How will they affect the Organization, and which threats require the most attention? Step 6: Security Risk Management Decisions What can be done about these risks? Step 7: Security Risk Management Implementation Procedural and budget aspects of implementing the agreed security risk management measures Step 8: Acceptable Risk Is the risk acceptable in balance with the criticality of program activities? Step 9: Follow up and Review Are the measures working? Is the assessment of risk now similar to how it was projected? Security Risk Management follows these basic steps with unique documentation to assist in each step. This course will explain each step of the risk management process and how each step interacts with other steps.
The structured approach to SRM
Human beings make subjective risk evaluations daily, but research shows that these evaluations are often inaccurate. This is because risk can be counterintuitive. A common mistake is the “optimistic bias,” whereby people believe that they will not be the victim of an adverse incident because it has never happened to them before. Most people find it impossible to imagine themselves as the victim of a dangerous event and say, “it won’t happen to me.” Another common mistake is “danger habituation,” also known as “complacency.” As the dangers increase and become frequent, people get used to them, become complacent, and neglect to take the necessary security precautions. Because people’s perceptions of risks vary widely, various decision-makers in an organization may not be making risk decisions in line with an organization’s overall risk strategy. These errors can lead to unnecessary activity cancellation, or worse, death or serious injury.
Here are a few examples of the dangers of subjective risk evaluations:
- I have never had a mobile phone stolen from me before; it should be safe to carry mine hooked onto my belt, even though the area I am entering appears rather seedy.
- I don’t need bars on my windows and doors as no intelligent person would attempt to break into my house as I am a big person with a powerful physique.
- It is not a problem checking into a cheap hotel in a questionable neighborhood as the locals will not want to attract the attention of the police by robbing me.
- I don’t require security measures when visiting the primary locations in the volatile region. The local culture would never permit an attack there because children may be killed or injured.
To reduce the problems that come with subjective risk evaluations, risk needs to be assessed structurally. A structured approach ensures a more comprehensive analysis, leads to better decisions, and limits errors in subjective evaluations and biases. The analytical concepts behind the assessments done in the SRM process are called Deconstruction and Externalization.
- “Deconstruction” breaks the problem down into its component parts. In the SRM process, most steps are deconstructed into as few variables as possible, with precise definitions of terms that allow for approaching the problem in a standard way. An example of this is how Risk is “deconstructed” into its component or core parts of Likelihood and Impact.
- “Externalization” takes the problem and puts it into a format that can be visualized and adjusted in a standardized, structured way. When completing the various steps covered in this course, we provide a method to help “externalize” the variables and assess them.
The aim of the structured approach in the SRM is that the process be:
- Fact-based, logical, and systematic
- Globally applicable in a consistent, de-politicized manner
- Reliable (achieve similar results when different people use it)
- Valid (accurately represent the security environment on the ground)
- User-friendly without being over-simplistic
By conducting the analysis this way, it is more likely that an analysis done by different people for the same location will be consistent. In addition, the structured nature of the process provides a basis for specific discussions of differences when they arise. Finally, the structure allows the assessment process to be more efficient, freeing up time for security practitioners to understand and analyze the security environment and its problems. Having an assessment “externalized” onto a matrix, for example, with each assessment represented by numbers, also allows for a “validity check.” This is a mechanism to see if there are any anomalies or differences that stand out between the issues being assessed. Structured tools often open themselves up to manipulation. At no time should any of the options in any of the steps of the SRM Process be chosen to achieve the desired result from that step or any other result? Any attempt to “retrofit” an assessment will corrupt the SRM process.
Conclusion
For managers to achieve their organizational goals, they must approach security risk in a structured way. The risk-management approach to security simplifies security risk management and saves costs by managing security risks effectively.