Introduction
The Threat Assessment is the process by which one identifies and assesses those actors and actions in the geographical area that may potentially cause harm to the organization. Using the threat-related points generated during the Project Assessment, it is necessary, in conjunction with the Security Department/Contractor, to list events that may block success (i.e., threats). In the operational context, a security professional, and especially security analysts, if available, are the key players in the threat assessment process to guarantee that senior managers get the best information on which to base their decisions.
There are two phases of Threat Assessment in the SRM process. The first, the General Threat Assessment (this page), assesses various categories of threats in the SRM Area from the organization’s perspective. The second, the Specific Threat Assessment, evaluates the specific level of threat to the organization in the form of distinct undesirable events that could occur and affect the organization.
This page will explain the first level of Threat Assessment and how they are conducted.
(The second level, Specific Threat Assessment, is covered in-depth in the next lesson)
General Threat Assessment
The General Threat Assessment aims to provide an objective description of the prevailing security threats and hazards in the environment of the SRM Area.
To ease understanding and discussion, the General Threat Assessment is broken down into four Threat categories as follows For the purpose of easing security policy development:
- Armed Conflict – protracted confrontation involving military hostilities conducted by force of arms between parties to a conflict involving one or more governmental forces and/or formed nongovernmental armed groups that take place within the territory of a state or between two or more states.
- Terrorism – an act involving (destructive) physical violence intended to cause damage to person(s) and/or public or private infrastructure, when the purpose of such act, by its nature or context, is to intimidate or to compel a state, population or organization to undertake or to abstain from undertaking any specific actions.
- Crime – an act that is forbidden by public law and that makes the offender liable to punishment by that law, including violent crime, when an offender uses or threatens force upon a victim, in which the violent act can be both the objective as well as the means to an end.
- Civil unrest – (also known as a civil disorder or civil strife) broadly refers to one or more forms of agitation or protest caused by a group of people involving disruption of social order or normal daily life activities. The protest can be peaceful or involve violence and can take the form of legal or illegal actions which include, but are not limited to demonstrations, strikes, sit-ins and other forms of obstructions, property damages, sabotage, petitions, riots, boycott, and rebellions. It can be local or widespread and escalate into general chaos. It often seeks to give visibility to alleged human rights violations or major socio-political or socio-economic problems and/or to advocate for a change in policy or government structure.
Each of the four threat categories is assessed on three variables on a 1-5 scale:
- Intent The motivation or disposition of a threat actor to cause the threat event as described
- Capability The capacity or ability of threat actors to cause the threat event as described.
- Inhibiting Context (factors in the geographical area which inhibit Intent, Capability or both)
Examining threats in this manner provides a common basis to describe each threat according to its willingness to do harm, its ability to do harm, and the aspects of the environment, such as the norms of the community or the capacity of the host government or local authorities, which may constrain or encourage a threat. In this way, Intent and Capability are “drivers” in the threat, and Inhibiting Context is a “restrainer” of the threat.
As with the threat variables above, History and Severity/Intensity are “drivers” in the hazard, and Warning/Preparedness is a “restrainer” of the hazard.
To ensure reliability (i.e., that the assessment will achieve similar results when different people conduct the assessment), each threat category (Armed Conflict, Terrorism, Crime, Civil Unrest) has distinct descriptors for subjectively rating each of the three variables (Intent, Capability, and Inhibiting Context). Below are the ranking matrices for each of the five categories in the General Threat Assessment.
Armed Conflict
| Intent | Capability | Inhibiting Context | |
| 1 | No intention to use armed/military force | No or very limited presence of hostile military-type capability (no or very limited military-type weapons, training, etc.) | Strong deterrent against initiating conflict |
| 2 | Indications that military force is seen as an option or statements threatening attack but a political solution still possible | Small arms/Automatic (light) Weapons (AK47, mortars, RPG) but minimal military-type training/experience and loosely organized | Pressure/other incentives/agreements against hostilities |
| 3 | Clear statements on imminent attack and peaceful options exhausted | Organized and structured forces with increased mobility and/or standoff/indirect (medium) weapon capability | Peace talks or unstable peace/cease-fire agreement |
| 4 | Isolated / Limited / Sporadic armed conflict occurring | Organized and structured forces w/ Heavy Weapons deployed and/or large numbers of forces and intensified military operations | No restraint/pressure to prevent continuation or outbreak of conflict |
| 5 | Full-scale armed conflict occurring | Organized structured forces with Heavy Weapons deployed or a large number of forces fully engaged. | Armed conflict is already occurring in the area. |
Terrorism
| Intent | Capability | Inhibiting Context | |
| 1 | Intent to use terrorism against the organization acknowledged | No known terrorist capability (threats and harassment only tactic) | Security forces effective |
| 2 | Intent to use terrorism and/or small-scale attacks | Limited to small-scale/individual basic operations | Security effective and/or social support of the cause |
| 3 | Wide-spread small-scale attacks on local infrastructure | Some isolated but coordinated operations which produce limited effects | Security moderately effective and/or active assistance to terror cells in some areas |
| 4 | Sustained or large-scale attacks and/or statements or actions demonstrating intent to target the Organization | Demonstrated capacity in a wider range and varied terror attacks | Security forces challenged to prevent terrorist activities |
| 5 | A group has already attacked the organization and is still operational in the area. | Demonstrated ability in all terror tactics to produce mass destruction and/or casualties (complex attacks) | Minimal ability to deter terrorist attacks. Terrorists have safe-havens. |
Crime
| Intent | Capability | Inhibiting Context | |
| 1 | Property crime, seldom violent | Generally lone, unarmed criminals | Police/criminal justice system effective and crime is socially unacceptable |
| 2 | Opportunistic crime against individuals, seldom violent | Generally lone criminals, sometimes armed. | Crime is not socially acceptable; the police/Criminal Justice system not fully effective |
| 3 | Violent crimes focus on relatively affluent elements of the community | Lone, armed criminals and/or unarmed criminals operating in small teams | No major social constraints on crime; police/CJ system stressed |
| 4 | Widespread violent crimes | Armed criminals operating in small teams | The police/CJ system significantly challenged |
| 5 | Prevalence of violence w/frequent fatalities and/or focus on the organization | Organized, armed criminal gangs | Minimal social or Police/CJ controls on criminal activity. |
Civil Unrest
| Intent | Capability | Inhibiting Context | |
| 1 | Peaceful crowds only | <100 people | Effective crowd control or crowd self-controlled |
| 2 | Some crowds become disruptive | <500 people | Crowd control not fully effective |
| 3 | Crowds become violent/localized riots | <1000 people | Crowd control mechanisms stressed (numbers, equipment, etc.) |
| 4 | Extensive/widespread violent crowds/riots (organization possible target) | <5000 people | Challenged crowd control mechanism or some possibly to allow anti-organization protests |
| 5 | Violent crowds/riots targeting the Organization | 5000+ people | Minimal crowd control mechanisms |
Hazards
| History | Intensity/Severity | Warning/Preparedness | |
| 1 | Not prone to hazard events | Limited | Effective warning and preparedness systems in place |
| 2 | Hazard events occur occasionally | Moderate | Partial/limited warning and/or preparedness systems in place |
| 3 | Hazard events occur frequently | Severe | Warning and/or preparedness systems in place not fully effective |
| 4 | Prone to predictable hazard events and/or hazard event imminent | Devastating | Warning and/or preparedness systems are untested or unknown |
| 5 | Prone to sudden onset hazard events | Multiple and devastating | No warning and/or preparedness systems in place |
The General Threat Assessment requires the choice of one descriptor for each variable in each threat/hazard category. If it is difficult to choose between two descriptors, the SRM Tool allows the user to choose a “half point” between the two (e.g., 2.5 between 2 and 3). The scores for the three choices are added up to give a threat score for each Category. Here is an example using the Armed Conflict Category:
Example (Armed Conflict)
| Intent | Capability | Inhibiting Context | |
| 1 | No intention to use armed/military force | No or very limited presence of hostile military-type capability (no or very limited military-type weapons, training, etc.) | Strong deterrent against initiating conflict |
| 2 | Indications that military force is seen as an option or statements threatening attack but a political solution still possible | Small arms/Automatic (light) Weapons (AK47, mortars, RPG) but minimal military-type training/experience and loosely organized | Pressure/other incentives/agreements against hostilities |
| 3 | Clear statements on imminent attack and peaceful options exhausted | Organized and structured forces with increased mobility and/or standoff/indirect (medium) weapon capability | Peace talks or unstable peace/cease-fire agreement |
| 4 | Isolated / Limited / Sporadic armed conflict occurring | Organized and structured forces w/ HW deployed and/or large numbers of forces and intensified military operations | No restraint/pressure to prevent continuation or outbreak of conflict |
| 5 | Full-scale armed conflict occurring | Organized structured forces with HW deployed or a large number of forces fully engaged. | Armed conflict is already occurring in the area. |
In this example, the Intent score is 2, the Capability score is 3, and the Inhibiting Context score is 1. The total threat score for Armed Conflict is 6.
At this stage, it is important for the security professional to conduct a “validity check” by comparing the numerical rating made for each variable with the numbers given to other variables and for the same variable in different locations to see if there are any anomalies that render the overall assessment invalid. Simple questions like, “Does it make sense that the Capability rating for Armed Conflict in this SRM Area is higher than the Capability rating for Armed Conflict in that SRM Area?” help ensure consistency throughout assessments.
After the validity check, the total threat score is compared with the range of scores in the table below to get a Threat Rating. For the example above, with a threat score of 6, the Threat Rating for Armed Conflict in this SRM Area would be Low (between 5 and 7)
| Threat Score Range | Threat Rating |
| 3 – < 5 | Minimal |
| 5 – < 7 | Low |
| 7 – < 9 | Moderate |
| 9 – < 11 | Substantial |
| 11 – < 13 | High |
| 13 – < 15 | Extreme |
The results of the General Threat Assessment can be displayed as a graph to visually highlight which General Threat category rating is the highest. The graph can also display one threat category across multiple SRM areas or multiple threat categories for just one SRM area.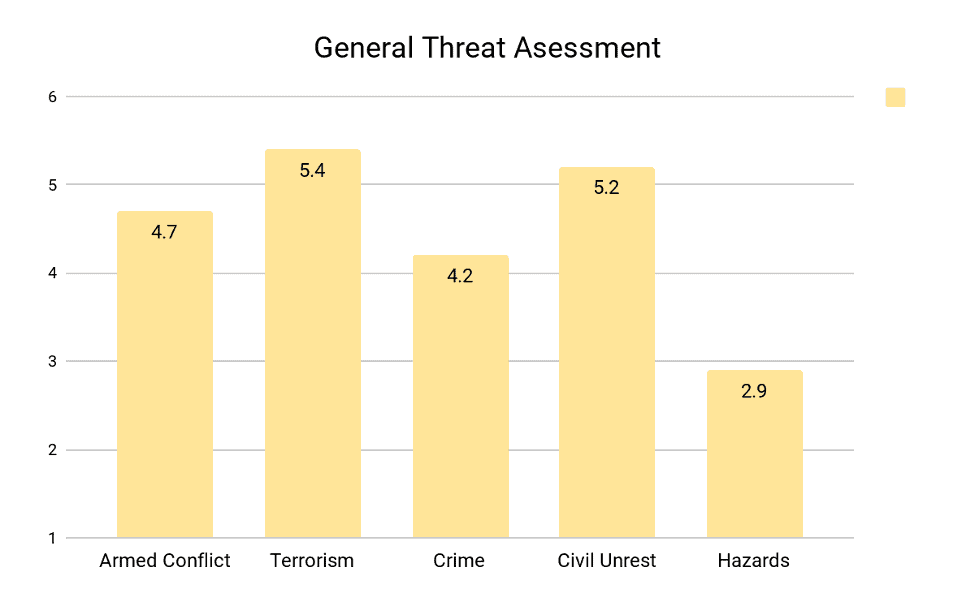
Conclusion.
It is important to emphasize the importance of familiarity and knowledge of the security situation in the area in which you wish to apply the SRM process. Each choice made in the General Threat Assessment must be based on credible facts, and the facts must be relative to the SRM Area for which the assessment applies (choices should also reflect threat-related information gathered in the Situational Analysis. Conducting the General Threat Assessment without a detailed understanding of the security environment, or using incorrect or erroneous information, will corrupt all the remaining steps of the SRM Process.
Annex D has detailed additional comments on all the threat descriptors. The descriptors and their supplemental information will also be available when using the SRM Tool.
It is important to note that the General Threat Assessment is not a predictive tool. It is based on current and historical information but does not try to anticipate future changes in the threat. It describes each category of threat and hazard as they exist now in the SRM Area. It does so by selecting the most appropriate descriptor for the variable being assessed. In addition to providing threat scores and threat ratings for each category, the General Threat Assessment can also produce a Security Level for that SRM Area. See Annex D for a description of how this process works.